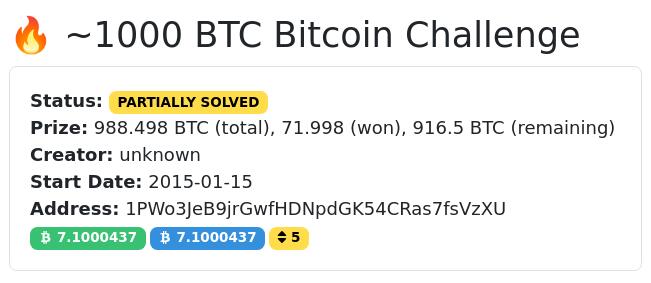
In 2015, an eccentric millionaire placed bitcoins in weak addresses.
For years, the prize has been contested by bots, GPUs, and in the future, it is expected to be the first target of quantum attacks.
The individual's goal was to monitor the advancement of computational power capable of breaking Bitcoin keys.
These keys have up to 256 bits of entropy, which can be understood as the difficulty of discovering them. They are simply large numbers, on the order of 2²⁵⁶.
He then created 160 addresses, each with fewer bits of difficulty, from 1 to 160, and placed a few satoshis in each one, doubling the amount in the next.
The total prize reached nearly 1,000 BTC. There are still 916 BTC left to be claimed.
The first few dozen addresses were quickly looted. There are bots monitoring the blockchain and stealing UTXOs that have some vulnerability — such as low entropy in the generation of the private key.
It was only at the end of 2015 that one of the owners of these bots noticed that the source of the bitcoins all came from a single transaction. He decided to share the discovery on the Bitcointalk forum, and that’s when more people began competing for the remaining prizes.
In 2019, the creator exposed the public keys of some addresses (those with indexes ending in 0 or 5). This is done simply by moving the coins—the key appears in the transaction. With it, other methods can be used, making it easier to crack.
One of these methods is a very old algorithm from 1978:
Pollard's Kangaroo Algorithm — a clever trick used to find private keys when part of the keyspace is known. Imagine two kangaroos jumping across a number line, one tame and one wild, eventually landing on the same spot. It’s a classic in cryptography, and now it's being used to chase Bitcoin prizes.
Since then, several programs and even participant "pools" have emerged, all trying to crack the next address. "kowala24731" secured an investment in the hundreds of thousands of dollars to rent GPUs and managed to break addresses #67 and #68 in early April.
Yesterday, someone, probably a beginner, cracked address #69 but didn’t secure the spending properly and exposed the public key.
In a few seconds, some bots cracked the key and replaced the transaction, battling for the balance. The last one paid a total fee of 1.2M sats.
The time to crack these addresses — discovering the private key from the public key — is quite short. A GPU can do it in less than a minute.
That’s why those who crack the keys can't publish it to the network; they must send it directly to a miner to include it in a block (like Mara).
Among the addresses with exposed public keys, the record was 130 bits of entropy, set by "RetiredCoder," who also cracked other keys.
These addresses are likely serving as "canaries in the coal mine" for the attacks Bitcoin may face. As long as there are still hundreds of BTCs sitting in them, yours should be safe.
